In 2010, American automakers introduced a new feature that allows owners to control the lock and start the engine through a smartphone at any corner of the globe. This connectivity needs to be dependent on telematics systems in cars, which are now standard on many models.
This article refers to the address: http://
Before the launch of the smartphone, a university research team released a research report that pointed out that by using the defects in the embedded system of the car, the key systems of the car (for example, brakes, engine throttles, etc.) are easy. Controlled maliciously.
These researchers have studied how to use "fuzzy" technology to invade critical systems from low-security networks. During the car's driving, there was a brake failure and engine runaway, indicating that the attack did put the passenger in danger.
Connecting a car to a wide area network is the culprit of introducing sophisticated attackers. A flaw can make a long-range attacker threaten a long queue of vehicles.
Researchers have not told us what we can do for today's embedded car safety. But as we will discuss later, we must make substantial reforms to automotive technology to better isolate network subsystems and life-critical security functions.
Today's automotive electronics
Figure 1 shows some of the electronic systems inside a contemporary car.
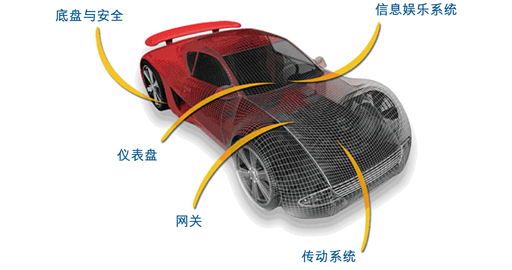
Figure 1: Part of the electronic system inside a contemporary car.
High-end luxury cars contain up to 200 microprocessors in a total of 100 components or corresponding systems of electronic control units (ECUs). These ECUs are connected by a number of different types of networks, such as Controller Area Network (CAN), FlexRay, Local Interconnect Network (LIN), and Media Oriented System Transfer (MOST). Automotive OEMs need to integrate ECU components and software from dozens of Tier 1 and Tier 2 suppliers. However, OEMs do not strictly control the development process of their suppliers.
So people will not be surprised if this situation cannot be sustained. OEMs will suffer the consequences of “cask theoryâ€: as long as an ECU with serious reliability problems can cause delays in delivery or vehicle failure, the reputation will be impaired.
Security threats and mitigation measures
Security threats to vehicles can be divided into three broad categories: local physics; remote; internal electronics. When these threats are added together, it often causes damage to the vehicle.
Local physical threat
An example of a local physical threat is by physically accessing the drive train CAN network and disrupting communication. This type of intrusive attack can easily damage the key functions of the car. However, a local attacker such as a dissatisfied mechanic can only damage a car and is therefore not enough to draw the attention of the design safety team. In addition, the complex electronic system of a car is difficult to truly guard against physical attacks. So we usually only pray for such threats.
However, there is an exception here: a private key is stored somewhere inside one or more ECUs to create a protected communication channel and provide local data protection services. Figure 2 shows some examples of long-range wireless connections used in next-generation cars.
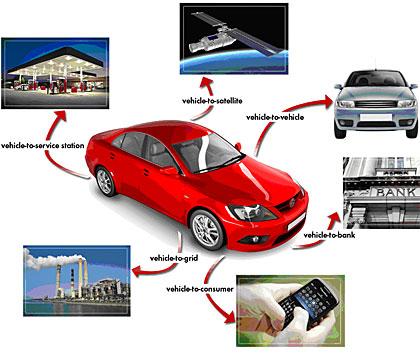
Figure 2: Long-range wireless connections used in next-generation cars.
Car algorithms, multimedia content, and confidential data may all require data protection. Private key storage must be able to withstand aggressive intrusions and non-intrusive physical attacks, because even losing only one "put" key can allow an attacker to establish a connection to a remote infrastructure, which can cause widespread damage there.
OEMs must be able to secure the key throughout the lifetime of the key generation and embedding it into the ECU, delivering it to the ECU and assembling it into the car, and then running around the street. Professional embedded encryption companies such as Green Hills Software, Mocana and Certicom can help OEMs and their suppliers through guidance and supervision in this area.
Remote threat
The following is a typical attack method: hackers find the way to access internal electronic systems by detecting the car's long-range wireless interface to find network security protocols, network services, and soft ribs in applications. Unlike data centers, cars generally cannot have full IDS, IPS, firewalls, and UTM. The recent incidents of invasion of Sony, Citigroup, Amazon, Google and RSA fully demonstrate that these defense mechanisms are ineffective in the face of sophisticated attackers.
In 2010, when Stuxnet (super factory virus) raged, General Keith Alexander, commander of the US Cyber ​​Warfare Command (CYBERCOM) under the US Department of Defense, proposed to build its own isolated security network for the important infrastructure of the United States, separate from the Internet. Although this approach seems too harsh, it is actually the idea we need. For driving safety, the car's critical systems must be completely isolated from non-critical ECUs and networks.
Internal electronic threat
Although physical network isolation is the ideal solution, touch points are inevitable. For example, in some markets, car navigation systems must be turned off while driving, which means that communication between systems with very different security standards is sensitive. In addition, there is a strong trend in design integration in the industry – using more powerful multi-core microprocessors to implement different systems, turning many ECUs into virtual ECUs – which increases the risk of software-induced threats, such as Privilege escalation caused by operating system defects, bypass attacks on cryptosystems, and denial of service.
Therefore, for safety, the car's internal electronic architecture must be redesigned. The interface between critical and non-critical systems and networks must be demonstrated and exhaustively analyzed at the highest management level and verified against the highest level of security standards such as ISO 15408 Evaluation Security Level (EAL) 6+ to confirm that there are no defects.
The High Reliability Software/Security Engineering Implementation Principles (PHASE) protocol supports the simplification of complexity, software component architecture, minimum privilege principles, security software and system development processes. OEMs must learn and adopt independent expert security verification, and It is implemented throughout the supply chain.
Summary of this article
Automakers and Tier 1 suppliers may not have made great efforts to consider safety requirements when designing cars that are currently on the road, but it is clear that the situation is changing. Manufacturers should work closely with embedded security specialists as early as possible in the design and architecture of automotive electronics and networks, and must improve safety-oriented engineering and software security. Finally, the automotive industry urgently needs an independent standards organization to define and implement system-level safety certification programs for in-vehicle electronic devices.
Transformer Accessories,Innovative Chip Radiator,High Efficiency Chip Radiator,High Temperature Resistant Transformer Bushing
Tianhong Electric Power Technology Co., Ltd , https://www.tianhongtransformer.com