In recent years, including the introduction of various software, the application of information technology in automobiles has become more and more extensive. Some cars are equipped with more than 100 electronic control units (ECU: Electronic Control Unit), and the program code is said to be about 10 million lines. The car has become a system equipped with a lot of software.
Cars that have become a software collective are now facing new threats (Figure 1). In 2010, researchers in the United States discovered that vulnerabilities in in-vehicle software can be attacked through communication channels inside and outside the car, thereby affecting the vehicle's control system. This shows that although real-time vehicle-mounted systems differ from information systems, in-vehicle software has weaknesses in information security in terms of authentication and communication security.
Moreover, the possibility of attacks on vehicle software systems will increase in the future. This is because the ways of attack are increasing. There are more and more types of vehicle external interfaces. In addition to the fault diagnosis function "OBD-II" and the charging control interface, it also includes functions linked to smartphones and tablet computers.
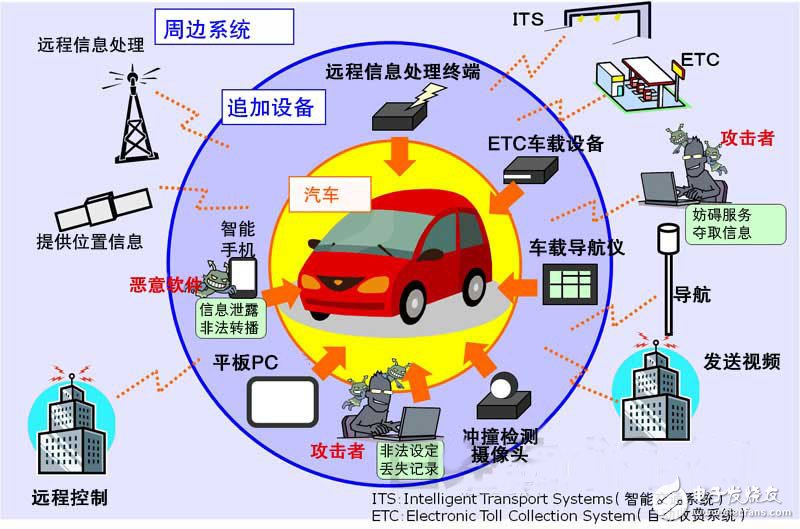
Figure 1: Automotive-related systems and threats
This article will introduce why automobiles need information security, analysis of automobile threats and countermeasures carried out by the Japan Information Processing Promotion Agency (IPA), and information security enhancement measures.
Why do cars need information security?
The use of information technology such as control software in cars is not new. As early as 1980, software with approximately 2000 lines of code was embedded in the ECU. So why do cars need information security today?
This is not only because the scale of the software mentioned in the opening chapter has increased thousands of times, but also with the three major trends in automotive technology.
The first trend is that with smartphones as the center, the linkage between cars and the Internet is becoming more common. A big difference between smartphones and traditional mobile phones is that customers can develop applications and provide them to anyone more freely. From simple applications to practical types, there are many types of applications on the market. Automotive-oriented applications have also appeared.
The problem is that some of these applications have poor reliability. Hackers may use the smartphone as a springboard through the loopholes to cause damage to in-vehicle equipment and in-vehicle navigation systems, or leak information in the car through the smartphone, infringing the privacy of the driver. Moreover, using a smartphone means that the car is always connected to an external network. Therefore, through external networks and smart phones, it is possible to launch an attack on the moving car.
In addition to smart phones, functions such as ETC (automatic toll collection system), smart car keys, etc., which are connected to the outside through wireless, and functions of pure electric vehicles (EV) to connect to the vehicle network via charging plugs are also gradually popularized.
In the future, as cars begin to access off-vehicle networks anytime and anywhere, it is an exaggeration to say that an attacker can attack the world's cars across the network without having to be close to the car. Even if it is not connected to the network anytime, anywhere, the malicious application of the smartphone that the user mistakenly downloaded may endanger the car.
Universal systems are widely used in vehicle equipment
The second trend is that the in-vehicle software and in-vehicle LAN are increasing the impact of basic control functions such as "driving, turning, and parking" of cars. For example, automobile manufacturers use communication or information terminals to provide services such as door lock control, engine power adjustment, and software update. Once these functions are successfully invaded by hackers, it is easy to cause major harm.
Moreover, in order to ensure versatility while reducing costs, some in-vehicle systems began to use general-purpose operating systems such as Linux. Car users are more and more convenient to use various services, but the difficulty of parsing and attacking the operating system is also getting lower and lower.
Not only the operating system, but the versatility of in-vehicle LANs is also improving. For example, the project "SEIS (Security Embedded IP-based System)" aided by the German government is considering the use of "Ethernet" for in-vehicle LANs and the use of the standard communication protocol "TCP / IP". In 2008, BMW adopted Ethernet as one of the vehicle diagnostic interfaces to rewrite the software.
In the past, represented by "CAN (Controller Area Network)", although the communication method of the vehicle-mounted LAN was standardized at the circuit level, most of the specific content such as request commands and response mechanisms differed by the company and constituted practical use "Barriers". But from the perspective of information security, such a "barrier" is actually a "firewall".
However, nowadays, adapters that provide in-vehicle LAN communication content using short-range wireless communication "Bluetooth", WLAN and other networks have appeared on the market. As more and more in-vehicle LANs adopt the Internet standard, many devices and information systems inside and outside the car will be closely connected to the car. Connecting to a car LAN is becoming easier, and breaking through a "firewall" has become a breeze.
Timeless situation
The third trend is that with the adoption of EV and ITS (highway traffic system) technology, the necessity of vehicles and external exchange of vehicle information is increasing. EV uses information processing technology to manage large-capacity storage batteries, and its role is to manage the state of charge and the number of charge and discharge of extremely expensive batteries.
One of the specific cases is a system that does not save the charging situation inside the EV, but stores it in a network server. The system collects data such as the number of charge and discharge of the battery and the amount of charge, and stores it on the server. Communication uses PHS and 3G / 4G mobile phones. In addition, the United States is also studying how to use EV charging status management information to implement services such as car sharing.
In addition, compared with gasoline vehicles, EVs have an environment with more power, and the on-board system that processes information will have more room to function.
Through the use of ITS technology, services to fully utilize vehicle information are also under discussion. Previously, it was confirmed that the road condition relied on cameras installed on the road. In the future, by sharing the information of each car, the driver is expected to grasp more detailed and accurate road conditions. To achieve this, car access to the Internet is a necessary condition. In addition, in order to promote the service, it is estimated that the calls for the formulation and disclosure of communication protocol standards will also increase.
Moreover, in the future, if ITS technology is applied to functions such as autonomous driving, in order to realize a convenient automotive society in which cars can be controlled by external information, ensuring information security will become increasingly important.
From an attacker's perspective, the three trends introduced earlier seem to be constantly creating conveniences for car hackers. Access to an external network will undoubtedly create an entry point for the attack; if the general-purpose system is popularized, the difficulty of the attack will be reduced; the diversification of services means that the car has a lot of information, and as long as valuable information is stolen, it can directly benefit.
Of course, as long as the car key and engine starting system can be hijacked, it is easy to steal the car. Moreover, the impact of car hijacking is not limited to individuals, and there are countless cars passing through the transportation facilities is one of the foundations of society. In the United States, Europe, and other places that vigorously combat terrorist activities, government-led research on automobile information security countermeasures is being promoted. Even from a socially stable perspective, taking safety measures for cars will become a must in the future. For companies involved in the development of automobiles, it is arguable that the relevant measures of automobile safety have been waiting.
Intelligent Secondary Equipment
Intelligent Secondary Equipments,Power Equipments,Portable Switchgear,Park Switchgear
Shandong Shunkai electrical equipment co., LTD. , https://www.chinasdsk.com