The rapid development of information technology brings convenience to life, and it also raises higher and higher requirements for security systems. Traditional door locks, security doors, monitoring and alarm systems, etc. always have problems such as inconvenient carrying, easy loss of damage, and easy password cracking. Therefore, the intelligent access control system using biometrics technology came into being. Among them, face recognition is the most intuitive recognition method in biometrics technology. It has the advantages of friendly, concealed, simple, accurate, economical and expansive and other identification technologies. The embedded system based on ARM technology is application-centric, and the software and hardware can be tailored to meet the strict requirements of the application system for function, reliability, cost, volume and power consumption, which has a great effect on saving cost and improving stability.
1 Development plan and design
1.1 Overall structural design
According to the characteristics of embedded technology and face recognition technology and its application concept in the access control system, the system determines the design and implementation of the face recognition subsystem of the embedded face recognition access control system, and performs image acquisition, embedded processing and Identify the response in three parts to study. First, the image information is collected by the camera; secondly, the CPU processing speed, technical indicators, and software support tools are selected, and the Samsung S3C2440A chip based on the ARM920T core is used. The operating system uses the latest and most stable free software embedded Linux operating system Ubuntu. The front-end ARM board implements these two functions. Finally, the face image is sent to the background database for face recognition, and the response information is fed back. The core part of face recognition, such as retrieval and recognition from data images, is done in the background. The overall structural design of its development plan is shown in Figure 1.
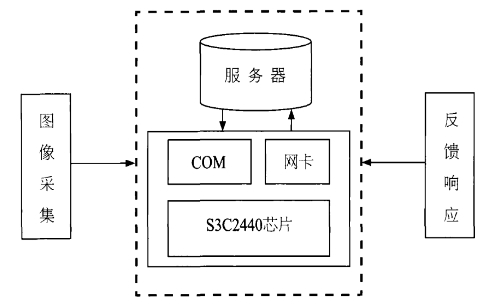
Figure 1 Overall design structure of the plan
1.2 kernel and operating system selection
The S3C2440A uses the ARM920T core and integrates the following on-chip functions:
1) 1.2V core, 1.8V/2.5V/3.3V storage, 3.3V expansion I/O, 16KB~ Cache (I-Cache)/16KB Data Cache (D-Cache)
2) External storage controller (SDRAM control box chip select logic)
3) Integrated LCD dedicated DMA LCD controller (supports up to 4K color STN and 256K color TFT)
4) 4 DMA controllers with external request pins
5) IIC bus interface (multi-master support)
6) IIS audio codec interface
7) AC, 97 codec interface
8) Version 1.0 SD main interface, compatible with 2.11 version of MMC interface
9) 2-way USB host control / 1-channel USB period control (ver1.1)
10) 4-way PWM timer / 1 internal timer / watchdog timer
11) 8-channel 10-bit ADC and touch screen interface
12) Camera interface (supports up to 4096x4096 input, 2048x2048 zoom input) As a GNU/Linux-based platform, Ubuntu is based on Debian and aims to create a new and consistent Linux system for desktops and servers. It includes a large selection of packages from the Debian distribution, while retaining Debian's powerful package management system for easy installation or complete removal of programs. Focus on safety and practicality. This system uses the version number Ubuntu 8.10. It has the advantages of virtualization, a complete Java stack, enhanced mail server capabilities, improved RAID support, a simpler Uncomplicated Firewall firewall, and a bundled Landscape client.
1.3 software process design
The choice of ARM core and Ubuntu system provides the basis for the implementation of system functions, and the system software controls the system functions. The design process of the system software is as follows. First, the camera monitors. If there is a moving object in front of the door, take a picture, and according to the brightness of the image, determine whether it is necessary to adjust the light, and perform automatic face detection and recognition after the image processing, if no matching image is found. The program returns to the camera monitoring state. If found, the door is opened; if there is no moving object, continue monitoring. If it is a visitor, you can apply for access through other means of the system. If someone in the room is controlled by the person in the room to open the door; if no one answers, the system prompts no one in the room, and collects photos of the person at the same time. Send function, send mail to the specified mailbox, and record the visit record.
2 Face recognition module design and implementation
The most critical implementation technology of this system is to complete the access control by performing face recognition. Firstly, the face is found from the still picture or the moving image, then the position of each feature point is determined and the feature is extracted. Finally, the face is compared with all the faces in the database, and the face is discriminated according to the fisherface decision rule. classification.
According to the nature of the input image, the face detection and recognition method is divided into two categories: the static method of the still image and the tracking frame method of the image sequence. According to the requirements of the face recognition technology, such as the hardware performance of the embedded access control system, the first major method is adopted. Several images of better quality are selected from the image sequence, and then the face recognition method of the still image is used. match. The static method is simple, fast and cost-effective.
2.1 Image acquisition and preprocessing
After the data is collected by the camera of the USB interface, the image is processed by the most basic image enhancement means. Image enhancement is to correct the grayscale of the acquired image by a series of means, or to filter the noise so that the grayscale of the image matches the grayscale of the actual scene as much as possible. It does not damage important information such as the outline and edges of the image, and makes the image clearer and visually sound. In order to reduce the influence of light, angle and other factors, median filtering and histogram equalization methods are adopted.
2.2 Face Detection and Location
Face detection refers to searching for a given still image or video sequence image by using certain strategies and methods to determine whether it contains a face, and if so, returning the position, size and posture of the face. Automatic, accurate and fast detection of face regions from image sequences is a key task in achieving system functionality.
At present, there are two main methods of face detection: one is a knowledge-based face detection method, and the other is a face detection method based on statistical learning. The statistical learning method is currently the mainstream method of face detection. Through a large number of face and non-face samples, some subtle differences between face images and non-face images are obtained. For the access control system, the background of the face detection target area is relatively simple, and the number and size of the face can be controlled, which greatly reduces the difficulty of face detection. First, the face feature search is positioned; secondly, the face region geometry is normalized, and again, the detected face is extracted.
2.3 Face recognition design and implementation
Face recognition is a problem of identifying high-dimensional and small-sample data. The difficulty of this kind of problem is that the number of training samples is very small. When the covariance matrix of the training samples is used as the estimation of the model covariance matrix, the following two problems will occur, one will cause a large deviation, and the other will cause a large deviation. It will make the intraclass covariance matrix singular.
In order to solve the problem that the intra-class covariance matrix singularity makes the matrix irreversible, many experts at home and abroad have proposed many classical algorithms. This system is adopted. A face recognition method based on structured fisherface. It applies the face recognition process of PCA and LDA. Firstly, the PCA reduces the dimensionality of the high-dimensional data, obtains the optimal feature representation of the original sample, and makes the intra-class covariance matrix of the sample non-singular, and then performs linear discriminant analysis. . Before the linear discriminant analysis is used, the dimension of the image vector is reduced by a given linear transformation in advance, thereby eliminating the singularity of the intra-class covariance matrix. The influence of external illumination interference, facial expression changes and other factors is largely solved. The advantage is that the face image has strong robustness compared to the feature face method in the case of illumination and expression changes. The personnel information in this system is managed by SQlite database technology. In the process of face recognition, the corresponding card number and face feature data need to be extracted from the personnel database. The personnel database stores basic information, face photos, and face feature data. The face feature data is the basis for face recognition, and the face photo is only used as a display recognition result, and does not participate in the recognition process.
3 system function test
The face recognition function uses the ORL face database commonly used in the world for testing. The ORL database consists of 10 images of 10 of 40 people each with different lighting, expressions and viewpoints. Eight people were selected for training and identification tests were conducted. The statistical results are shown in Table 1.
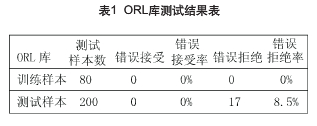
The experiment proves that the algorithm is a stable and efficient algorithm, which can realize the function of face recognition technology for access control.
4 Conclusion
The embedded face recognition access control system has become one of the most popular research topics in current scientific research and practical engineering applications due to its non-contact data acquisition, good concealment, convenience, convenience for post-tracking and strong interactivity. . This system was developed and implemented as a research project of Hebi City Science and Technology Bureau. The practicality and application prospect of the embedded face recognition access control system based on ARM technology is very broad.
Rack-mounted Terminal Box is ranging from 12 ports to 48 ports. It is suitable for the use in telecommunication network, central office optical cable system and premise fiber network. The rack mount patch panel with 2 cable entry ports on the back maximum is design in sliding structure. At the back of the box, there are 2 cable fixing bayonets. The spice tray inside the box is made of ABS material which available for 0.9mm, 2.0mm & 3.0mm Fiber Cable. Each Patch Panel is fully loaded with panels, adaptors, splices trays and accessories and is ready for installation.
Rack-mounted Terminal Box
Optical Terminal Box,Ftth Terminal Box,Rack Mounted Terminal Box,Wall Mounted Terminal Box
Chengdu Xinruixin Optical Communication Technology Co.,Ltd , https://www.xrxoptic.com